TL;DR: Zero-Knowledge Proofs (ZKP) have transitioned from cryptographic theory to a $7.5B market cornerstone. By validating information without exposing underlying data, ZKPs solve the "Privacy Paradox," enabling institutions like JPMorgan and Deutsche Bank to satisfy KYC/AML mandates while maintaining GDPR-compliant data sovereignty.
Who This Is For
This guide serves Chief Information Officers (CIOs), Enterprise Architects, and Compliance Officers who must balance aggressive regulatory reporting with modern data security requirements. It is essential reading for technical leaders transitioning from legacy data silos to privacy-preserving infrastructure.
Our Verdict
Zero-Knowledge Proofs are the definitive standard for 2025 enterprise security. They eliminate the "honeypot" risk by replacing raw personal data with cryptographic proofs. Organizations that fail to integrate ZK-architecture now will face unsustainable data liability costs and increased regulatory friction by 2027.
The $7.5 Billion Market: From Niche to Necessity
The global ZKP market is accelerating. Valued at $1.28 billion in 2024, it will reach $7.59 billion by 2033, growing at a 22.1% CAGR. The "Zero-Knowledge KYC" sector leads this surge, growing 40% annually as banks automate compliance without assuming data liabilities.
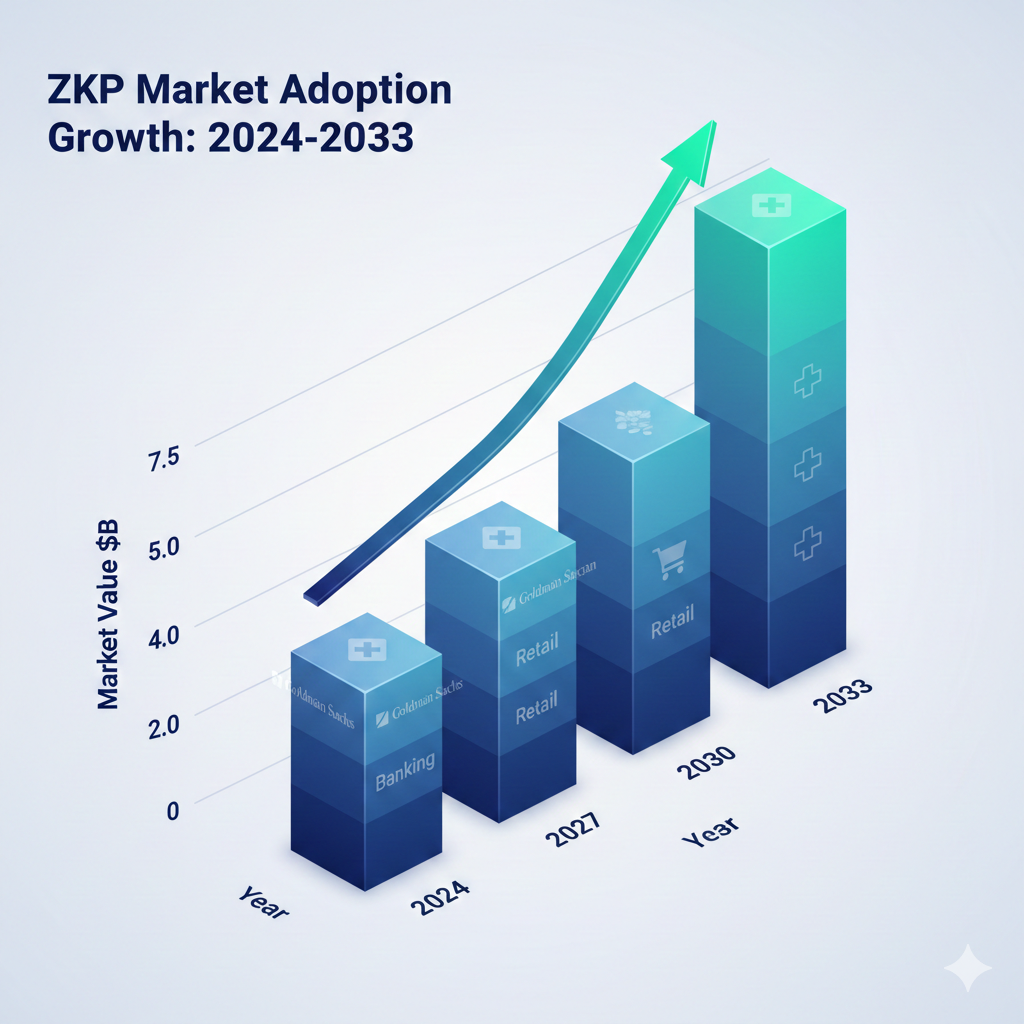
Goldman Sachs, Sony, and Nike have already integrated ZKP-based solutions for confidential asset validation. The infrastructure has matured: ZK-based Layer 2 rollups like zkSync and StarkNet now secure $28 billion in Total Value Locked (TVL), providing the throughput required for global finance.
Technical Pillars: SNARKs, STARKs, and zkVMs
Architects must master three primary engines driving the 2025 landscape:
- zk-SNARKs: The industry workhorse. Modern iterations like Halo 2 eliminate "trusted setup" vulnerabilities, enabling efficient verification on mobile devices.
- zk-STARKs: The future-proof alternative. Despite larger proof sizes, STARKs provide Quantum Resistance, ensuring data remains shielded against future quantum computing threats.
- zkVMs (Zero-Knowledge Virtual Machines): The most critical developer trend. By supporting Rust and C++, zkVMs allow enterprise teams to leverage existing DevOps talent rather than hiring specialized cryptographers to build custom circuits.
Recursive Proofs represent the most significant innovation for 2025. These "summaries of summaries" bundle thousands of transaction proofs into a single cryptographic package, allowing regulators to verify an entire day’s ledger in milliseconds.
Solving the Compliance Crisis
ZKPs resolve the conflict between reporting mandates (KYC/AML) and data protection laws (GDPR) through Selective Disclosure.
"Auditor Keys represent the future of banking transparency. They provide regulators with specific 'view keys' to audit history without exposing data to the public internet or vulnerable central databases."
Privacy by Design frameworks move data processing off-chain. Ledgers store only the cryptographic evidence of rule compliance. This strategy eliminates the "honeypot" risk; a server breach yields no raw Personally Identifiable Information (PII), drastically reducing corporate liability.
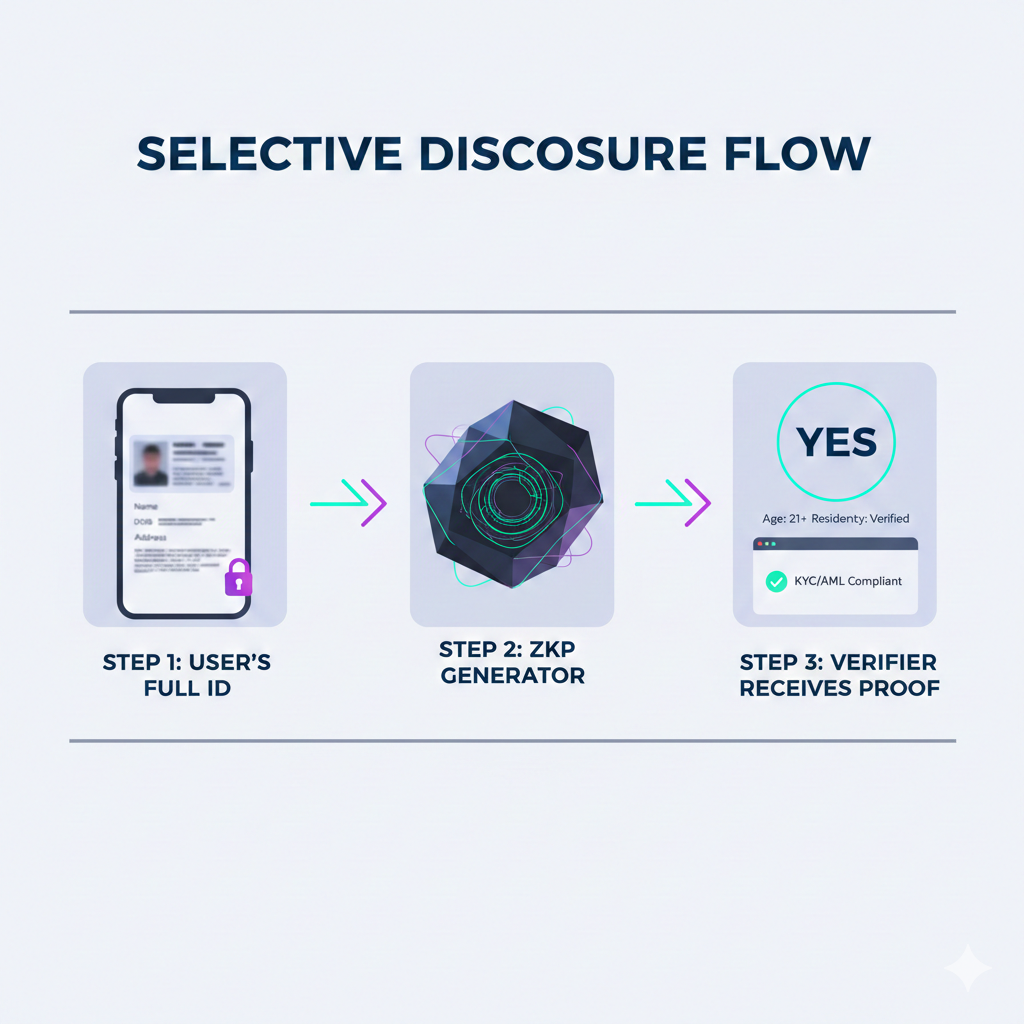
Adoption Hurdles
Computational Latency remains the primary bottleneck; generating complex proofs on mobile hardware takes 5 to 10 seconds. Furthermore, high-performance validator hardware costs often exceed $30,000.
However, regulatory clarity is arriving. NIST and the EU’s MiCA framework are codifying "cryptographic audits" as a legal standard, moving ZKP from an optional security feature to a mandatory compliance requirement.
The Future of Digital Sovereignty
By 2030, the convergence of ZKP and AI will allow firms to prove ethical model training without revealing proprietary weights. Enterprise leaders must audit current data intake processes immediately. Moving to a ZKP-enabled architecture is a strategic necessity to future-proof against the evolving threats of the digital age.
Key Takeaways
- Market Dominance: ZKP is a multi-billion dollar industry backed by global financial leaders.
- Data Sovereignty: Users prove identity or eligibility without surrendering sensitive raw documents.
- Risk Reduction: Storing proofs instead of raw data eliminates honeypots and aligns with GDPR data minimization.
- Technical Strategy: Use SNARKs for mobile efficiency and STARKs for long-term quantum security.



