TL;DR: A direct codebase compromise of Trust Wallet Browser Extension (v2.68) resulted in a $6–7 million theft between December 21 and 25, 2025. Attackers exfiltrated seed phrases via a hijacked analytics library. Users must transition to hardware isolation and Multi-Party Computation (MPC) to eliminate software-side single points of failure.
Who This Is For
This guide is essential for cryptocurrency investors using browser-based "hot" wallets and security professionals auditing supply-chain vulnerabilities. If you hold digital assets on internet-connected extensions, these protocols are your baseline for asset preservation.
The "December Blackout" of 2025 proves that software-based self-custody remains a high-risk entry point. While the cryptocurrency market reached a $12.2 trillion valuation this year, the Trust Wallet exploit demonstrates that attacker sophistication scales with market value. This incident is a mandatory case study for implementing "Defense in Depth" strategies.
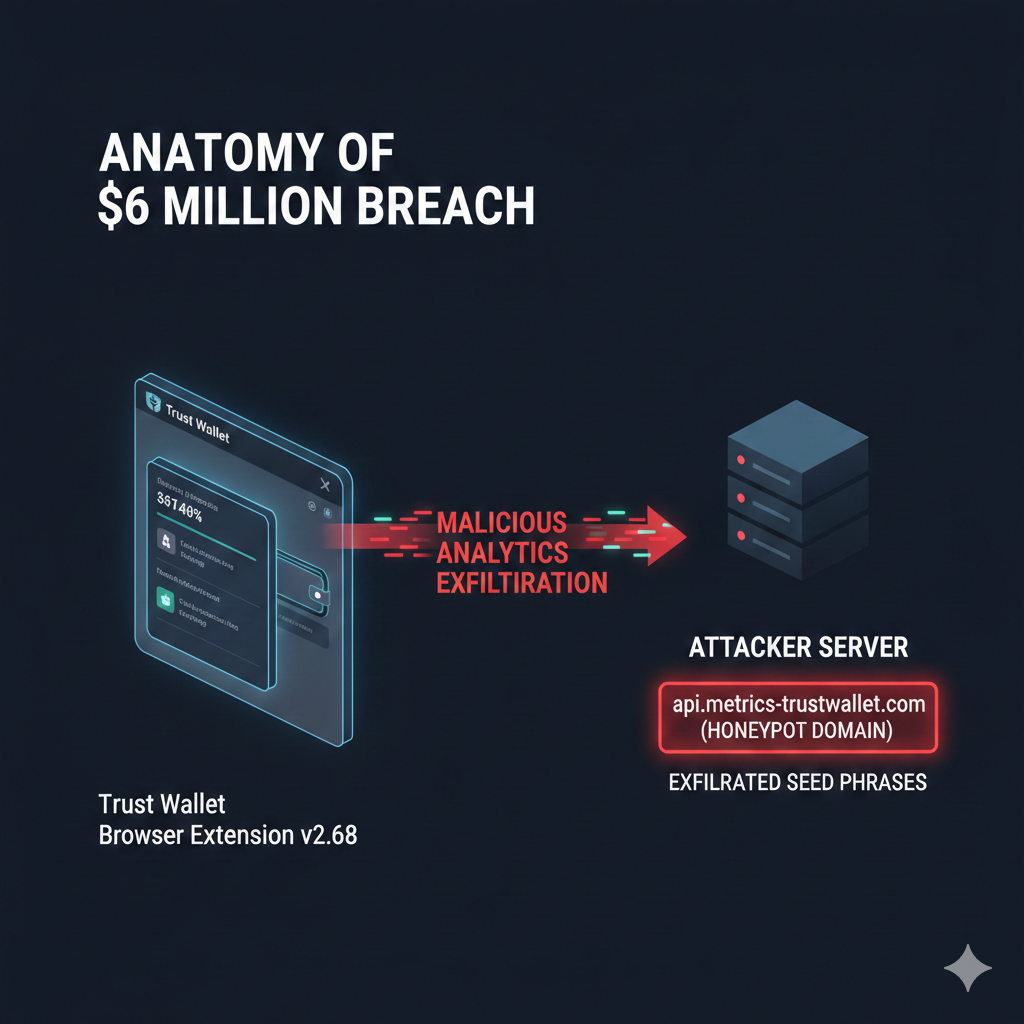
Anatomy of the $6 Million Breach
The compromise of Trust Wallet version 2.68 was a direct injection of malicious code into the extension’s internal codebase. This attack surpasses the 2023 WebAssembly (WASM) vulnerability (CVE-2023-31290) in technical severity; rather than guessing weak entropy, the software itself was weaponized against the user.
The exploit worked with surgical precision. Upon installation, the malicious update silently decrypted mnemonic phrases and exfiltrated them through the PostHog analytics library to an attacker-controlled server: api.metrics-trustwallet.com. Digital forensics show the domain was registered on December 8, 2025, confirming a pre-planned operation.
The Hot vs. Cold Wallet Reality
Hot wallets maintain a 78% market share due to DeFi convenience, according to Fortune Business Insights. However, as 69% of owners reported net gains in late 2025, the "honeypot" effect has peaked. Attackers now target the retail middle class through the software supply chain.
"The 28.3% CAGR growth in the cold storage sector suggests the market is finally acknowledging that software-only custody is insufficient for significant capital." — Fortune Business Insights
Adopt the 80/20 Rule of Storage: Maintain no more than 20% of liquid assets in a hot wallet. Keep the remaining 80% in hardware-isolated environments.
Hardening Your Security
To resolve the "Self-Custody Paradox," users must implement hardware and cryptographic isolation:
- Hardware Isolation: Devices like Ledger or Trezor ensure private keys never interact with internet-connected environments. Attackers cannot sign transactions without physical access to the device.
- Multi-Party Computation (MPC): MPC technology splits a private key into multiple shares. No single entity holds the full key, eliminating the single point of failure inherent in seed phrases.
- Manual Updates: Disable automatic updates for browser extensions. Wait for verified "all-clear" signals from security researchers like ZachXBT or SlowMist before updating wallet software.

The 2026 Outlook: Account Abstraction
The industry is moving away from the 12-word seed phrase. Account Abstraction (via EIP-7702) enables social recovery and biometric authentication. Furthermore, integrated on-chain scanners—which prevented $191 million in losses earlier this year—are now the industry standard for user protection.
Our Verdict
Software wallets are tools for utility, not storage. The Trust Wallet breach confirms that any browser-based extension is vulnerable to supply-chain injection. For any balance exceeding your monthly risk tolerance, hardware isolation is non-negotiable.
SAFU Reimbursement
Trust Wallet and Binance have invoked the SAFU (Secure Asset Fund for Users) protocol. Affected users on version 2.68 must document their transaction history and submit a claim through the official Trust Wallet support portal immediately for full reimbursement.
Key Takeaways
- Immediate Action: If you used v2.68, move assets to a new, clean wallet immediately.
- Isolate Keys: Treat hot wallets as cash and hardware wallets as the vault.
- Audit Permissions: Reject wallets requesting unusual permissions or connecting to unverified analytics domains.
- Upgrade Strategy: Transition to MPC or EIP-7702 solutions to remove mnemonic vulnerabilities.



